Sophos has 23 repositories available. Follow their code on GitHub. Skip to content. OpenVPN is an open source VPN daemon C 2,063 0 0 0 Updated Apr 6, 2020. Openvpn-build Forked from OpenVPN/openvpn-build OpenVPN Build NSIS 206 1 0 0 Updated Apr 6, 2020. If you haven’t already set up users on your network, you will need to implement at least. 1) Close all active VPN tunnels 2) Download and install the TAP driver above or from OpenVPN. 3) Right-click on this file: C:Program Files (x86)SophosSophos SSL VPN Clientbinopenvpn-gui.exe and choose properties - compatibility – run as administrator - Press OK 4) Reboot PC and try again. Download and connect with the OVPN file Download file from user portal Download Configuration for Other OSs in.ovpn format. Double-click the configuration file to open it in Tunnelblick.
This guide will explain how to setup SSL VPN to access your home network (LAN). While the Sophos website has an official “SSL VPN Remote Access” How-To video, it’s missing some important steps. I’d recommend watching the video as it’s fairly short and following this guide.
Dynamic DNS
Openvpn Sophos Utm
If you do not have a static WAN IP address, create a Fully Qualified Domain Name (FQDN) using a Dynamic DNS service. There are free services available such as DuckDNS.org but Sophos also offers its own DDNS service for free.
1. Open the ‘Dynamic DNS’ tab on the ‘Network’ page and click ‘Add’.
2. Type in your desired FQDN in the ‘Hostname’ field. It must end with *.myfirewall.co if using Sophos as your DDNS service provider (ex: myname.myfirewall.co).
3. Select your WAN ‘interface’ (likely Port2) and choose ‘NATed Public IP’ next to ‘IPv4 Address’ and set the ‘IP Edit Checking Interval’ as desired (default value of ’20’ works fine).
4. Select ‘Sophos’ as the ‘Service Provider’ and click ‘Save’. After about 3-5 minutes, try accessing or pinging your newly created FQDN.
Setting up SSL VPN
1. Setup your hostname. Open the ‘Admin Settings’ tab on the ‘Administration’ page and type in your FQDN or WAN IP address in the ‘Hostname’ field (ex: myname.myfirewall.co) and click ‘Apply’. The reason for this is that when you download the VPN configuration file, it uses this hostname as the address your device will try to access. There is also an option to use a different hostname which will be explained later.
2. Create a user account. Open the ‘Users’ tab on the ‘Authentication’ page and click ‘Add’. Fill out the ‘Username’, ‘Name’, ‘Password’ and ‘Email’ fields. ‘User Type’ can be set as desired (leaving the default setting of ‘User’ will suffice). Select ‘Open Group’ under the ‘Group’ drop down which is simply a default group Sophos XG created during setup that allows for unlimited access at all times. The remaining fields can be left to their default settings. Click ‘Save’ at the bottom.
3. Create an IP Host. Open the ‘IP Host’ tab on the ‘Host and Services’ page and click ‘Add’. Enter a ‘Name’ as desired (i.e. ‘Local subnet’), select ‘IPv4’ for ‘IP Version’ and select ‘Network’ for ‘Type’. In the ‘IP Address’ field, enter your subnet address (i.e. 172.16.16.0) and select the appropriate ‘Subnet’ (i.e. /24 255.255.255.0). Click ‘Save’ at the bottom.
(Optional) Create another IP Host using an IP Range that the VPN connection will use (default is 10.81.234.5 to 10.81.234.55). This can be utilized for the ‘Source Network and Devices’ in the firewall rule during Step 7 for increased security.
4. Setup SSL VPN. Open the ‘SSL VPN (Remote Access)’ tab on the ‘VPN’ page and click ‘Add’. Type in a ‘Name’ and ‘Description’ as desired and add your user account created in step 2 to the ‘Policy Members’. Additionally, add the IP Host created in step 3 to the ‘Permitted Network Resources (IPv4)’ section. Everything else can be left to the default settings. Click ‘Apply’ at the bottom.
5. Adjust VPN settings. On the same page (VPN), click the ‘Show VPN Settings’ on the top right section above the tabs. Set the ‘Protocol’ to ‘UDP’ (not required but recommended for better VPN performance). As mentioned in Step 1, you can add your FQDN or WAN IP address to the ‘Override Hostname’ field. This will likely be required for your VPN configuration file to use the correct address, so it’s recommended to just type in your FQDN or WAN IP address again. Click ‘Apply’ at the bottom.
6. Enable SSL VPN. Open the ‘Device Access’ tab on the ‘Administration’ page and make sure ‘SSL VPN’ is checked for LAN and WAN. You can also check ‘HTTPS’ for VPN if you want access to the Sophos XG web UI you’re currently using when connected through VPN. Click ‘Apply’ in the ‘Local Services ACL’ section you just modified.
7. Create a firewall rule for VPN. Open the ‘Firewall’ page and add a ‘User/Network Rule’. Fill in the applicable fields and set ‘Source Zones’ to ‘VPN’, ‘Source Network and Devices’ to ‘Any’ or the IP Host for the VPN IP range created in the optional step, ‘Destination Zone’ to ‘LAN’ and ‘Destination Network’ to the IP Host you created in Step 3 (i.e. ‘Local subnet’). Other settings can be setup as desired. See my previous post on Firewall Rules for more information.
Setting up OpenVPN
At this point, VPN is setup on Sophos XG and now you just need to configure your client that will be used to VPN into your home network. In this example, we’ll use an iOS device.
1. Download ‘OpenVPN’ on your iOS device from the App Store.
2. Open the web browser on your iOS device and browse to the same IP address used to configure Sophos XG except on port 443 (ex: https://172.16.16.16:443) which should bring you to the Sophos User Portal. Log in using the account created earlier and download the configuration file for iOS.
3. Open the configuration file in the OpenVPN app on your iOS device. The remainder of the steps should be self explanatory as you simply need to add the configuration file to OpenVPN, fill in your username and password and click connect at which point you’re now able to connect to your local network from outside the network.
Setting up an OpenVPN server with Sophos UTM and Viscosity
Openvpn Sophos App
This guide will walk you through the steps involved in setting up an OpenVPN server on a Sophos UTM host that allows you to securely access your home/office network from a remote location and optionally send all of your network traffic through it so you can access the internet securely as well.
Sky go pc app login. Before using this guide, we highly recommend you read through our Introduction to Running an OpenVPN Server Article.
For this guide, we assume:
- You have already installed the latest version of Sophos UTM (9.5 at time of writing)
- Sophos UTM has been set up with at least a WAN interface and a LAN interface
- You are connected with your client device to the Sophos UTM server via its LAN interface during this guide
- This installation of Sophos UTM is a fresh install
- You already have a copy of Viscosity installed on your client device
If you need to download and install a copy of Sophos UTM, information can be found at https://www.sophos.com/en-us/support/utm-downloads.aspx. We won't be covering the details of setting up a Sophos UTM instance, many guides can be found online. If you are running a different version of Sophos UTM, it's very likely that many or even all of the steps outlined in this guide will still apply. If you are looking to setup an OpenVPN server on a different operating system, please check out our other guides.
Your client device needs to be connected to the Sophos UTM server via the LAN interface. This is necessary so that you can access the WebAdmin portal to set up the Sophos UTM configuration. The specifics of how you can achieve this depend on your particular network configuration.
If you don't have a copy of Viscosity already installed on your client machine, then please check out this setup guide for installing Viscosity (Mac | Windows).
Unfortunately we cannot provide any direct support for setting up your own OpenVPN server. We provide this guide as a courtesy to help you get started with, and make the most of, your copy of Viscosity. We've thoroughly tested the steps in this guide to ensure that, if you follow the instructions detailed below, you should be well on your way to enjoying the benefits of running your own OpenVPN server.
Sophos offer technical support for UTM at https://secure2.sophos.com/en-us/support.aspx
First you need to log in to the WebAdmin portal from your client device connected to the LAN interface of the Sophos UTM server. Open a browser on your client and navigate to the IP address of the LAN interface of your Sophos UTM server (something like https://10.0.0.1:4444 or https://192.168.0.1:4444). You will need to login. The password for the admin user should have been configured when you set up your Sophos UTM instance.
Authentication Services
If you are using a user authentication system, such as LDAP, you will need to add those settings to authenticate your users.
- On the side bar, click
Definitions & Users>Authentication Services. - In the Automatic User Creation section of the Global Settings tab, check the Create users automatically checkbox.
- Click
Applyto save this change. - In the Automatic User Creation for Facilities section below, check the Client Authentication option.
- Click
Applyto save this change. - Click on the Servers tab and then click on the
New Authentication Server..button. - Enter the details of your user authentication system and click
Savewhen done.
Local User Authentication
If you are not using an authentication system, you will need to create a local user account for each user so that they can access the User Portal and connect to the VPN.
- On the side bar, click
Definitions & Users>Users & Groups. - In the Users tab, click
+ New User... - Fill in the user's details, including Username. Set the Authentication to
Localand provide a password. - Leave the Use static remote access IP unchecked.
- When you are done, click
Save.
Next we need to define the VPN subnet, so that users can be assigned IP addresses:
- Still in the
Definitions & Userssection of the side bar, click theNetwork Definitionssubsection. - In the Network Definitions tab, click
+ New Network Definition... - Give the network a name, we will use 'VPN Network'.
- Leave the type as
Networkand set the IPv4 address to 10.8.0.0. - Leave the Netmask as
/24 (255.255.255.0). - When you are done, click
Save.
To allow users to log in to the User Portal:
- On the side bar, click
Management>User Portal. - In the Global tab, click the grey power button in the top right. It will change to yellow as it starts up.
- In the Allowed Networks box, click the folder icon.
- From the side bar, drag
Internal (Network)into the Allowed Networks box to allow users to connect to the User Portal via the internal network. - Click
Applyto save these changes. The power icon should subsequently turn green.
To allow VPN users to pass their DNS requests through the VPN:
- On the side bar, click
Network Services>DNS. - In the Global tab, click on the folder icon in the Allowed Networks box.
- Click and drag the VPN Network created above into the Allowed Networks box.
- Click
Applyto save this change. - Click on the Forwarders tab.
- Deselect the Use forwarders assigned by ISP checkbox.
- In the DNS Forwarders box, click on the
+icon to add a network definition. - Give the network a name. We will be using Google's DNS servers, but you're free to use a different DNS server.
- Leave the type as
Host. - Set the IPv4 address to the DNS server of your choice, 8.8.8.8 in our example using Google.
- Click
Saveto add the DNS server. - If you want more than one DNS server, add it now, repeating the steps above.
- When you are done, click
Applyto save the changes.
To configure the OpenVPN server:
Openvpn Sophos Free
- On the side bar, click
Remote Access>SSL. - In the Profiles tab, click
+ New Remote Access Profil... - Enter a name in the Profile name input, we will call our server 'OpenVPN server'.
- In the Users and Groups box, click the folder icon. A list of available users and groups will appear in the side bar. Click and drag the user created above (or the authentication service users, i.e. LDAP Users) into the Users and Groups box.
- In the Local Networks box, click the folder icon. A list of local networks will appear in the side bar. Drag any networks that should be reachable by the user into the Local Networks box. To allow users to access the local network, drag in
Internal (Network). To allow users to access the internet via the Sophos UTM server, drag inExternal (WAN) (Network). - Uncheck the Automatic firewall rules option, we will set out own firewall rules.
- Click
Save.
Next click on the Settings tab at the top:
- In the Interface address input, click the trash icon to remove the current value.
- Click the folder icon to show a list of available networks. Drag any networks that the client is allowed to connect via into the input box. In our case, we will drag in
Internal (Address). - Set the Protocol to
UDP. - Set the Port to 1194.
- In the Override hostname input, enter the local network address of the Sophos UTM server, 10.0.0.1 in our example.
- Click
Applyto save these changes. - In the Virtual IP Pool section, click on the Pool network folder icon.
- Drag in the VPN Network we created earlier.
- Click
Applyto save these changes.
If you wish to allow users to maintain simultaneous connections to the OpenVPN server, leave the Allow multiple concurrent connections per user option selected. Otherwise, deselect it and click Apply to save that change.
Now click on the Advanced tab at the top:
- Change the Encryption algorithm to
AES-256-CBC. - Leave the Authentication algorithm as
SAH1. - Leave the Key size as
2048 bit. - If you have a local SSL certificate to identify the server to the clients, select it in the Server certificate drop down.
- Leave the Key lifetime as 28800.
- Click
Applyto save these changes. - Under Compression Settings, untick 'Compress SSL VPN traffic', then click
Apply.
To ensure the connected clients will use the server for DNS resolution:
- Still in the
Remote Accesssection of the side bar, click theAdvancedsubsection. - Set the DNS server #1 to 10.8.0.1, which will be the OpenVPN server's IP address.
- Click
Applywhen done.
The firewall needs to be configured to allow our VPN and User Portal traffic.
- On the side bar, click
Network Protection>Firewall. - In the Rules tab, click
+ New Rule... - In the Sources box, click the folder icon.
- Drag in from the side bar any users we created previously that we want to be able to access the User Portal.
- Click on the folder icon in the Services box.
- Drag in
HTTPSto allow the users to access the User Portal via HTTPS. - Click on the folder icon in the Destinations box.
- Drag in
Internal (Network)to allow users to access the User Portal via the local network. - Leave the Action as
Allow. - Click
Savewhen done.
Now enable this rule by clicking the small grey power switch icon next to our new rule. It should change to green to indicate the firewall rule is now applied.
Next we need to create a masquerade rule, so that we can pass traffic through the VPN and out onto the external network interface.

- Still in the
Network Protectionsection of the side bar, click theNATsubsection. - In the Masquerading tab, click
+ New Masquerading Rule... - Click the folder icon next to the Network input.
- Click and drag in the VPN Network we created earlier.
- Change the Interface input to
External (WAN). - Leave the Use address input as
<< Primary address >>. - When you are done, click
Saveto create the rule. - To activate the rule, click the greyed out button next to the rule so that it changes to green.
To connect to our OpenVPN server, we need to download the client configuration for our user. On the client machine:
- Open a browser and navigate to
https://your-server-ip. - Enter the Username and Password for the user and log in.
- Click on the Remote Access tab.
- Click on the
Downloadbutton next to 'Click here to download the configuration file to set up SSL VPN on Linux, MacOS X, BSD or Solaris'. - It should download a file called '[email protected]'.
The interface provided by the Mac and Windows versions of Viscosity are intentionally very similar. As such, we will focus our guide on the Mac version, pointing out any differences with the Windows version as they arise.
Xbox 360 controller ps4 remote play download. If you do not have Viscosity already running, start Viscosity now. In the Mac version you will see the Viscosity icon appear in the menu bar. In the Windows version you will see the Viscosity icon appear in the system tray.
Click the Viscosity icon in the menu bar (Windows: system tray) and select 'Preferences..':
This shows you the list of available VPN connections. We assume you recently installed Viscosity, so this list is empty. Click on the '+' button and select Import Connection > From File..:
Navigate to the location of the '[email protected]' file and open it. You will see a pop up message to indicate that the connection has been imported.
Sophos Ssl Vpn App
Configuring the Connection
Double click on the connection in the Preferences window to bring up the connection settings. You will now need to set the connection parameters as outlined below:
- Click on the Networking tab and enter '10.8.0.1' into the 'Servers' field in the DNS Settings section.
- Click the
Savebutton to save these changes.
(Optional) Allowing Access to the Internet
By default the VPN connection will allow access to the file server and other computers on the home/office (LAN) network. However if you also wish to have all internet traffic sent through the VPN connection it's necessary to make a final edit to the connection:
- Double-click on your connection in the Viscosity Preferences window to open the connection editor
- Click on the Networking tab.
- Click the 'All Traffic' drop down and select the 'Send all traffic over VPN connection' option. It is not necessary to enter a Default Gateway.
- Click the
Savebutton.
Connecting and Using Your VPN Connection
You are now ready to connect. Click on the Viscosity icon in the menu bar (Windows: system tray) and select 'Connect DemoConnection'. You will be prompted to enter the username and password. Enter them and press OK. That's it, you should see a notification that you're now connected!
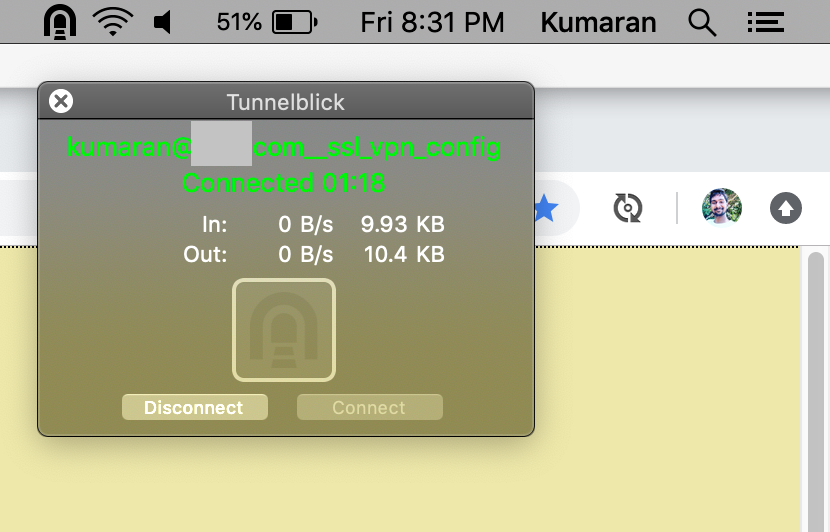
To check that the VPN is up and running, you can use the Viscosity details window. Click the Viscosity menu bar (Windows: system tray) icon and select 'Details..'. This will bring up the details window.
This window will show you the traffic passing through the VPN connection.
Accessing Network Resources
Sophos Vpn Ssl Client Download
Once connected to your VPN, you can access your files or other services by using the LAN IP address you would use if you were connected to them via your home/office local network.
Sophos Client Vpn
Connect via Mac
To connect to a shared network directory from your Mac connected to the VPN:
- Open a Finder window
- Click Go on the menu bar and select 'Connect to Server..'
- In the Server Address, type the LAN IP address of your network resource (something like 192.168.0.x) and click
Connect. - Enter the username and password for the network resource
- Select the shared volume you want to access and click
OK
Openvpn Sophos
Network resources you would normally find appearing in the Finder sidebar will not appear when connected to via the VPN. You can find connected network resources in the Computer directory. In a Finder window, press ⌘ + shift + c to jump to the Computer directory.
Connect via Windows
To connect to a shared network directory from your PC connected to the VPN:
- Type the
lan-ip-addressinto the Search the web and Windows box in the taskbar and pressEnter(something like 192.168.0.x) - Enter the username and password for the network resource
- You will then see the folders shared by this host
That's it, you've set up your very own OpenVPN server. Congratulations, you are now free to enjoy the benefits of operating your own OpenVPN server!
