Ransomware continues to be a top cyber threat, with 30% of organizations admitting having been victimized in the past IT security is the responsibility of everyone within an organization. It falls on IT managers, therefore, to educate their workforces to best safeguard against attacks when they happen. Notice 2011-64.
John mccain book faith of my fathers. You can exclude an application from exploit detection, either in response to a detection or in advance of any detection.
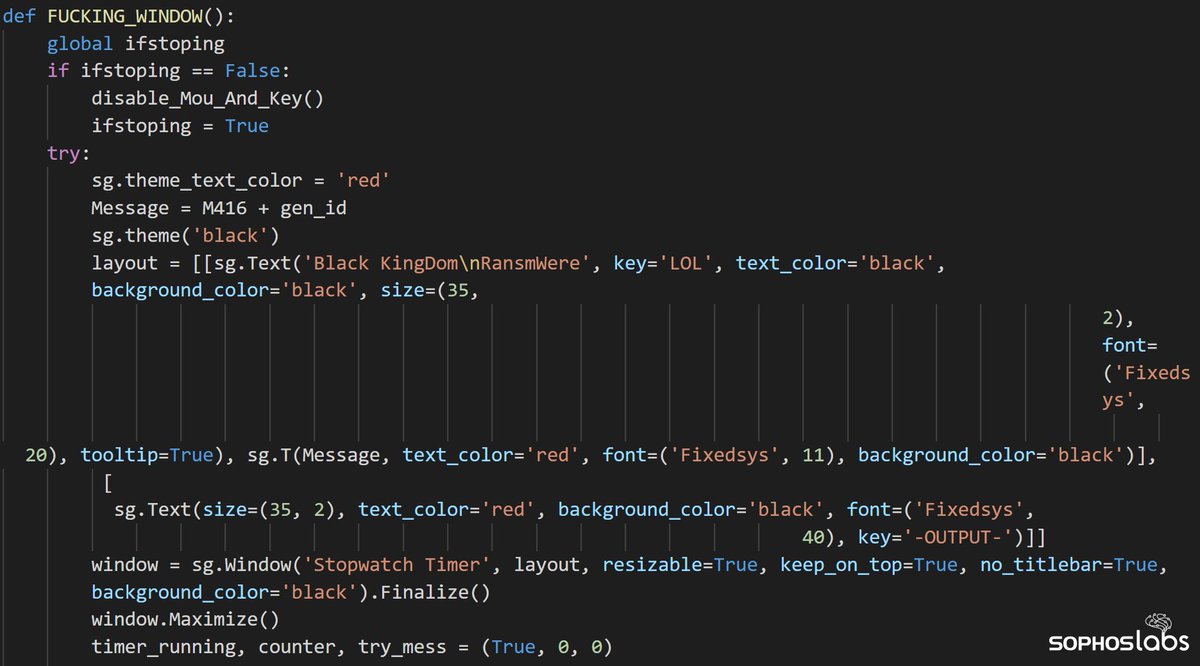
Introduction
Remote detection is triggered when the ransomware is remote to the server, but attacks files contained on the server, such as a share. The remote computers triggering the attack may be: Windows computers managed in Sophos Central where Intercept X is installed. Windows computers managed in Sophos Central where Intercept X is not installed. Sophos EDR gives you the tools to ask detailed questions when hunting down threats and strengthening your IT security operations posture. You get access to powerful, out-of-the-box, customizable SQL queries that access up to 90 days of endpoint and server data, giving you the information you need to make informed decisions. You can run Sophos Clean on a server from Sophos Central. Go to Sophos Central, go to Alerts, and mark the alert as resolved. What to do if you see 'Remotely-run ransomware detected ' We detected ransomware running on a remote computer and trying to encrypt files on network shares. The main menu lists the functions available to you in Sophos Central. The Dashboard is the start page of Sophos Central and lets you see the most important information at a glance. Either in response to a detection or in advance of any detection. Stop detecting ransomware.

You can set exclusions for a specific event, a specific exploit, or all exploits associated with an application.
Stop detecting an exploit that's been detected (using events list)
If an exploit is detected on an application but you're sure the detection is incorrect, you can stop it happening again by using options available in your events list. Yota for mac os.
This applies to all your users and computers.
To stop detecting an exploit, do as follows:
- Go to Computers or Servers, depending on where the application was detected.
- Find the computer where the detection happened and click it to view its details.
- On the Events tab, find the detection event, and click Details.
- In Event details, look for Don't detect this again and select an option:
- Exclude this Detection ID from checking. prevents this detection on this application. It adds an exclusion for the Detection ID associated with this specific detection. If the same behavior occurs again on your estate, this doesn't trigger a detection. However, if the behavior is different, for example different paths or files, the Detection ID is different and requires a separate exclusion.
- Exclude this mitigation from checking this application. prevents any checks for this exploit on this application. This increases the risk of a attack. However, it can be useful where specific business applications generate many unexpected detections.
- Exclude this application from checking. prevents any checks for any exploits on this application. This carries the most risk and therefore you should only use this as a last resort.
- Try excluding the Detection ID first as that is better targeted. If the same detection happens again, exclude the exploit. If the same detection still happens, exclude the application.
- Click Exclude.
Sophos Malware Detection
We'll add your exclusion to a list.

Sophos Ransomware Detection
Detection ID exclusions go into the Global Exclusions. Application exclusions go into the Exploit Mitigation Exclusions.
